TLP AMBER
New Zealand Health
Sector Cyber Event
Response Plan
under the Official Information Act 1982
Released
February 2019
TLP AMBER
TLP AMBER
Purpose
1. The purpose of this plan is to outline the New Zealand health and disability sector’s process
for managing and containing major cyber events; and to minimise their impact on locally and
nationally critical operational; clinical; and patient data sets, and information technology
systems, in order to maintain the delivery of “front-line” health services, while preserving
public trust and confidence.
NOTE: this plan is marked as TLP AMBER. This means that recipients of this plan may only
share it with members of their own organisation who need to know, and only as widely as
necessary to act on it.
Context
2. Over the recent period, the global health sector has experienced an increasing trend of major
cyber events, security incidents, and data breaches; industry predictions suggest
ransomware attacks on healthcare organisations — the No. 1 cyber-attacked industry — will
quadruple by 20201. In past year, the most notable of these incidents was the global “Wanna
Cry” ransomware outbreak in May 2017; this cyber event almost operationally crippled the
UK’s National Health Service. Closer to home, the New Zealand health sector has also
recently been impacted by cyber events.
3. It should be noted that a security incident is considered to be one of a range of cyber events
that is covered under this plan. Various examples of health sector-wide cyber events that fall
within the scope of this document may include:
• major disruption to operationally vital or critical local or national digital health systems
(i.e. ransomware, or Internet connectivity failure);
• attempts to gain unauthorised access to national digital health systems (e.g. hacking);
• nationally critical health data-sets (e.g. National Health Index) are altered or deleted
under the Official Information Act 1982
without authorisation by the data “owner”;
• virus or other malicious malware attacks (suspected or actual) that prevent the delivery
of public-facing front-line clinical services; or
• damage or loss of access to critical national digital health systems due to theft; fire;
natural disaster; or catastrophic systems/physical infrastructure failure.
Released
New Zealand health sector-wide cyber event response plan
4. An effectively implemented, resourced and tested health sector wide cyber event response
plan is a vital part of maintaining maintain public trust in the health sector; and the security,
privacy, and availability of New Zealand’s digital health systems.
NOTE: this plan should not be used to manage sector-level privacy breaches; the process
required to manage this type of incident is distinctly different. Furthermore, it should also be
1 https://www.csoonline.com/article/3153707/security/top-5-cybersecurity-facts-figures-and-statistics.html
TLP AMBER
TLP AMBER
noted that this plan is not intended to replace the already nationally embedded Coordinated
Incident Management System (CIMS) health sector-wide model of emergency management;
rather it is expected that plan will form a context-specific response model within the wider
CIMS framework.
5. The New Zealand health sector-wide cyber event response plan consists of two phases:
i.
Phase One: local/organisational-level cyber event response, and national sector-level
impact assessment; and
ii.
Phase Two: local cyber event severity escalation to the national-level, and health
sector cyber event plan activation.
Phase One: local health sector entity cyber event response and severity impact assessment
6. Each health sector entity must have an established and tested internal cyber event response
plan in place so that the potential severity of an incident can be triaged as early as possible.
(Core requirements for an effective cyber event response plan appear at Annex B).
7. Typically all cyber events will initially present themselves as local issues. On this basis, every
potentially affected health sector entity will immediately triage each cyber event they
experience, and respond to it in accordance with their own internal event response plan.
8. As part of this local incident triaging process, the affected health sector entity must also
simultaneously consider the following sector-wide impact criteria:
i.
does this event also have the ability to compromise the
confidentiality of patient
identifiable or clinical information held within critical local or national digital health
systems2?; or
ii.
does this event have the ability to compromise the
integrity of information required
under the Official Information Act 1982
to deliver local or national public-facing/front-line operational or clinical services?;
or
iii.
does this event have the ability to materially affect the
availability of either locally or
nationally critical digital health data or information and systems required to deliver
public-facing/front-line operational or clinical services?; or
Released
iv.
does this event have the ability to compromise the
trust and confidence of the public
in relation of the affected health sector entity’s ability to deliver operational or
clinical services?;
v.
does this event have the ability to potentially
involve the use of public funding in
relation to cyber-crime activities (i.e., the payment of ransomware)?;
2 Examples of a national digital health system would be NHI; HPI; NBSP; NSS; or Connected Health.
TLP AMBER
TLP AMBER
vi.
is it possible this event could separately present itself again in a similar fashion
elsewhere in the health sector?; or
vii.
does this event have the ability to attract
public attention in the near-term to the
extent that it could lead to Chief Executive or Ministerial-level interaction with the
media?
9. Depending on the outcome of this severity assessment process, two action pathways will
emerge:
i.
the incident remains categorised as a localised event that is being responded to solely
by the affected health sector entity, and the NCSC/CERT NZ and MoH are notified for
situational awareness only; or
ii.
one or more of the sector-wide impact criteria listed above are met, meaning the
incident is assessed to be of sufficient severity and potential consequence that it
could represent a potential threat to multiples DHBs or wider public health and
safety.
10. Should the second action pathway be initially identified as the most likely, the affected
health sector entity will immediately
contact the relevant MoH POC(s) listed at Annex C.
Furthermore, should the event also be considered a possible cyber
security incident, the
specified NCSC/CERT NZ POCs [listed at Annex C] will also be contacted.
Phase Two: activation of the New Zealand health sector cyber response plan
11. At this point, the affected health sector entity in partnership with MoH [and NCSC/CERT NZ
if necessary] will further assess the potential severity of the technical, personal health
information, clinical, legal, financial, and policy/reputational impact(s) of the cyber event at
hand.
under the Official Information Act 1982
12. If the cyber event continues to be assessed at sufficient severity and potential consequence
that it could represent a potential threat to multiple DHBs/PHOs/NGOs, or wider public
health and safety, the RACI table at Annex A will be utilised to guide the joint decision-making
required to collectively manage the cyber event at a sector-level.
13. Within the context of the RACI table-led approach, MoH’s core function will be to co-
Released
ordinate external communications; stake-holder engagement; and strategic-level advice
regarding the incident across, and on behalf of, the health sector. These objectives will be
achieved by:
a. supporting the affected health sector in its external communications and engagement
regarding the event;
b. leading the provision of advice to the Minister(s) (in partnership with the affected health
sector [and the NCSC/CERT NZ if necessary]); and
TLP AMBER
TLP AMBER
c. acting to protect and preserve critical national digital health systems and capabilities.
It is important to note these MoH functions will be undertaken collaboratively with, and in
support of, the affected health sector entity. (It is not intended that the MoH will carry out
an operational role.)
14. Beyond the affected health sector entity(s) and MoH, other parties likely engaged within a
health sector cyber event will be as follows:
Organisation
Role
Responsibilities
National Cyber
to protect and respond to cyber incidents • given the varied nature of cyber security
Security Centre
affecting important information infrastructures,
emergencies, and size and mandate of various
cyber incidents that pose a threat to New
health sector entities, the operational lead
Zealand’s national security, cyber incidents, and
agency will vary, but will typically be NCSC or
1982
cyber incidents that have been perpetrated by
CERT NZ;
an advanced persistent threat actor.
• input into communications and advisory
Act
CERT NZ
to undertake New Zealand-wide incident
activities undertaken by MoH and/or the
response and triage, situational awareness and
affected health sector entity;
information sharing, advice and outreach, and • provide specialist technical cyber security
coordination of serious cyber security incidents.
incident response capabilities [NCSC only]
National Cyber
to provide policy advice to Ministers regarding • provide advice to Ministers regarding cyber
Policy Office
national-level cyber incidents.
incident communications, and ministerial
[DPMC]
involvement require to help response efforts.
Government
provides government and the public with • leads the delivery of ICT 'system-wide'
Chief Digital
assurance and confidence that ICT risks and
assurance and advice across government, as
Information
Office [ICT
processes in the State services are identified
part of government’s overall assurance
Assurance]
and managed effectively.
framework; and
• provide assurance oversight of District Health
Boards’ ICT capability programmes.
Official
15. Assessing the potential severity of a health sector cyber event will require equal consider
both its technical and non-technical attributes. To this end, the following factors should be
the
considered:
➢ Are there any risks to public health and/or safety?;
➢
under
How clinically/commercially/personally sensitive is the information?;
➢ What is the context of the information involved?;
➢ Was the information encrypted or otherwise inaccessible?;
➢ How might the compromised information be used?;
Released
o could it be used for fraudulent or harmful purposes?;
➢ Was any third-party information involved?;
➢ Is there a risk of ongoing breaches?
➢ What is the number and nature of affected persons that could be affected?;
➢ Might the information have been lost or stolen?;
➢ Has the information or item been recovered?;
➢ Could the data have been tampered with?;
TLP AMBER
TLP AMBER
➢ Is this an isolated event, or could it be a symptom of a wider systemic problem?;
➢ Does this event create a litigious issue that now needs to be managed?; and
➢ Does this event involve financial loss?
---------------------------------------------------------------------------------------------------------------------------------
“All-of-Government” national response to a health sector cyber security event: National Cyber
Security Emergency Plan (CSERP) activation
NOTE: if a health sector cyber event is confirmed as a cyber
security incident, the following
supplementary escalation pathway will likely be followed:
16. At the outset, it is not the intention of the CSERP to remove the decision-making ability of
MoH or affected health agencies; it is designed to be enabling and provide a framework for
coordinated responses. In other words, MoH and the affected health sector agency should
always retain the right to take all event response decisions as they relate to clinical systems
and patient safety.
17. If a confirmed health sector cyber security incident is mutually triaged at a LOW or MEDIUM3
level, the operational response by central government agencies [beyond MoH] will be
limited to technical advice and assistance from CERT NZ or NCSC.
18. Due to the dynamic nature of cyber security events, the categorisation may change
throughout its “life”. If at any stage a health sector cyber security event is re-triaged at HIGH,
a National Cyber Incident Coordination Group meeting being should convened. These
Groups are cyber-security focused, and sit below the activation of the National Security
System.
19. National Cyber Incident Coordination Group meetings are typically chaired by Director: CERT
NZ, Director-General: GCSB, or Director: National Cyber Policy Office, or by a senior
representative from New Zealand Police (or by suitable delegates). The MoH will likely
under the Official Information Act 1982
attend as a representing the affected national sector in the form of the MoH’s Group
Manager: National Digital Systems and/or Group Manager: Digital Strategy and Investment.
It is at this point where it is also likely that the Minister of Health [and Minister Responsible
for the GCSB potentially also] would be formally briefed on this development.
20. If the incident is triaged at CRITICAL, the National Security System may be triggered in the
Released
form of activating the CSERP. This involves a series of formal national-level coordination,
response, advisory, and communications activities. These actions would include the
convening a Watch Group and possibly CE-level Officials Domestic and External Security
Committee meetings.
21. Further detail on the activation of the National Cyber Security Emergency Response Plan is
held by the National Cyber Policy Office.
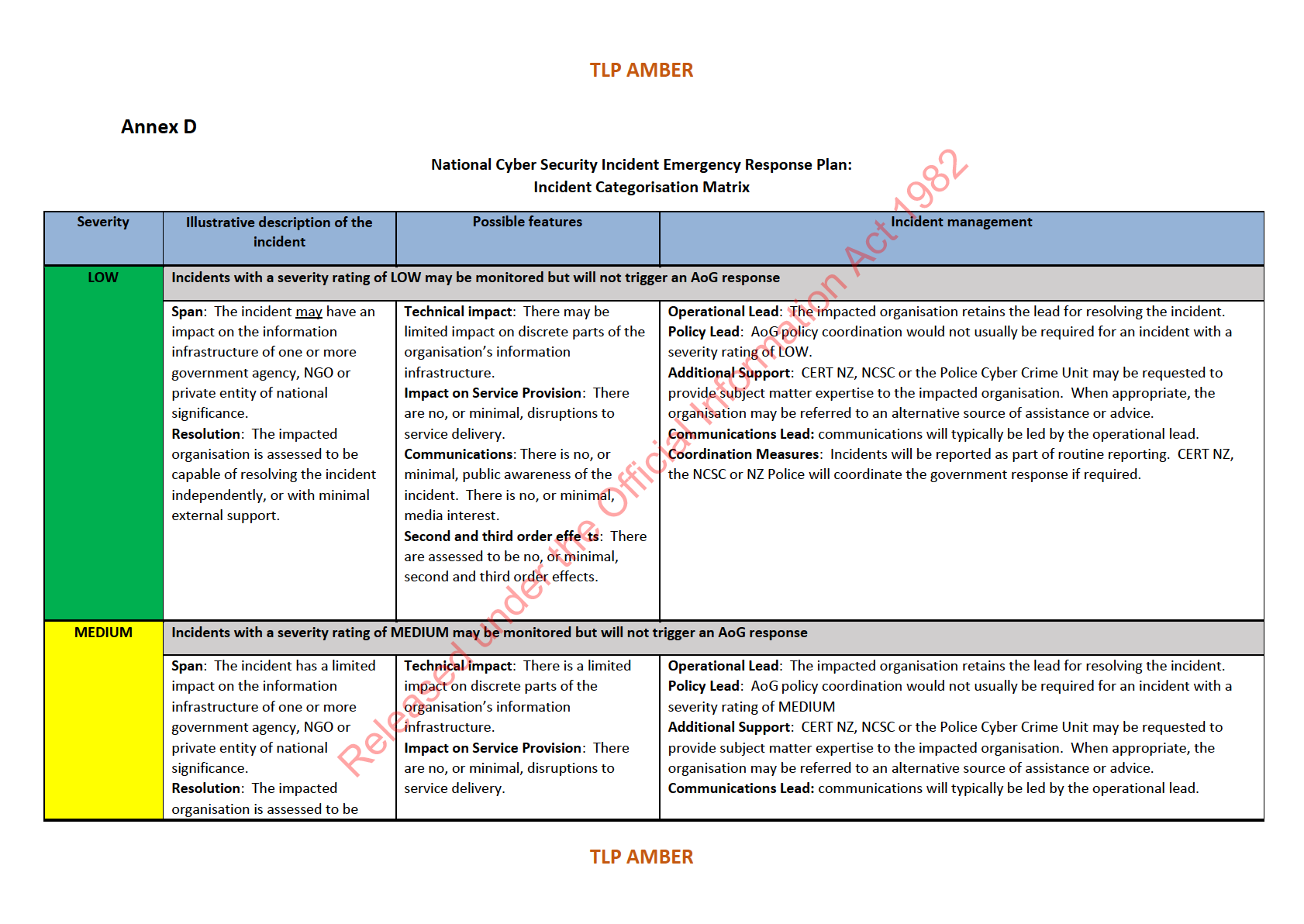
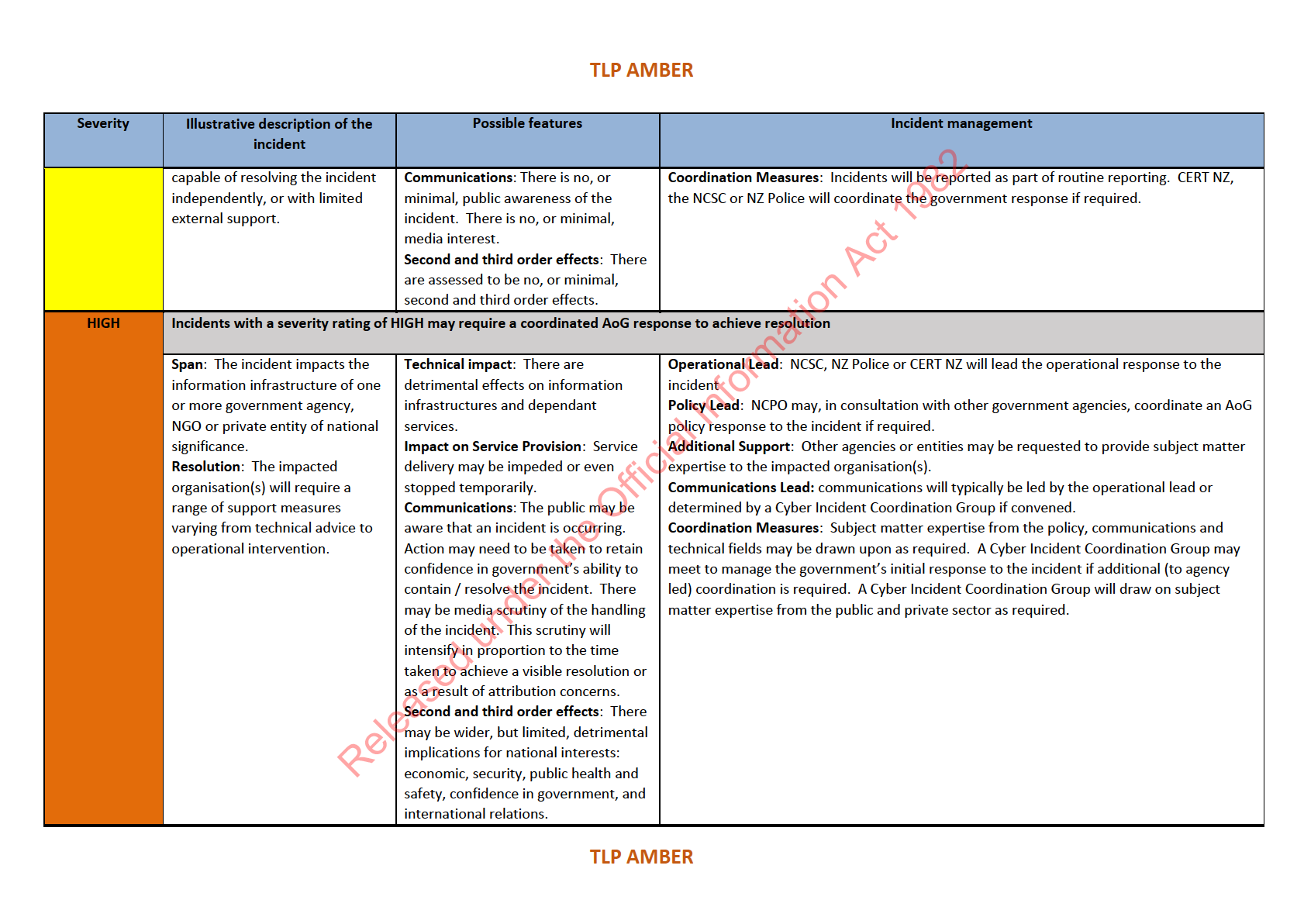
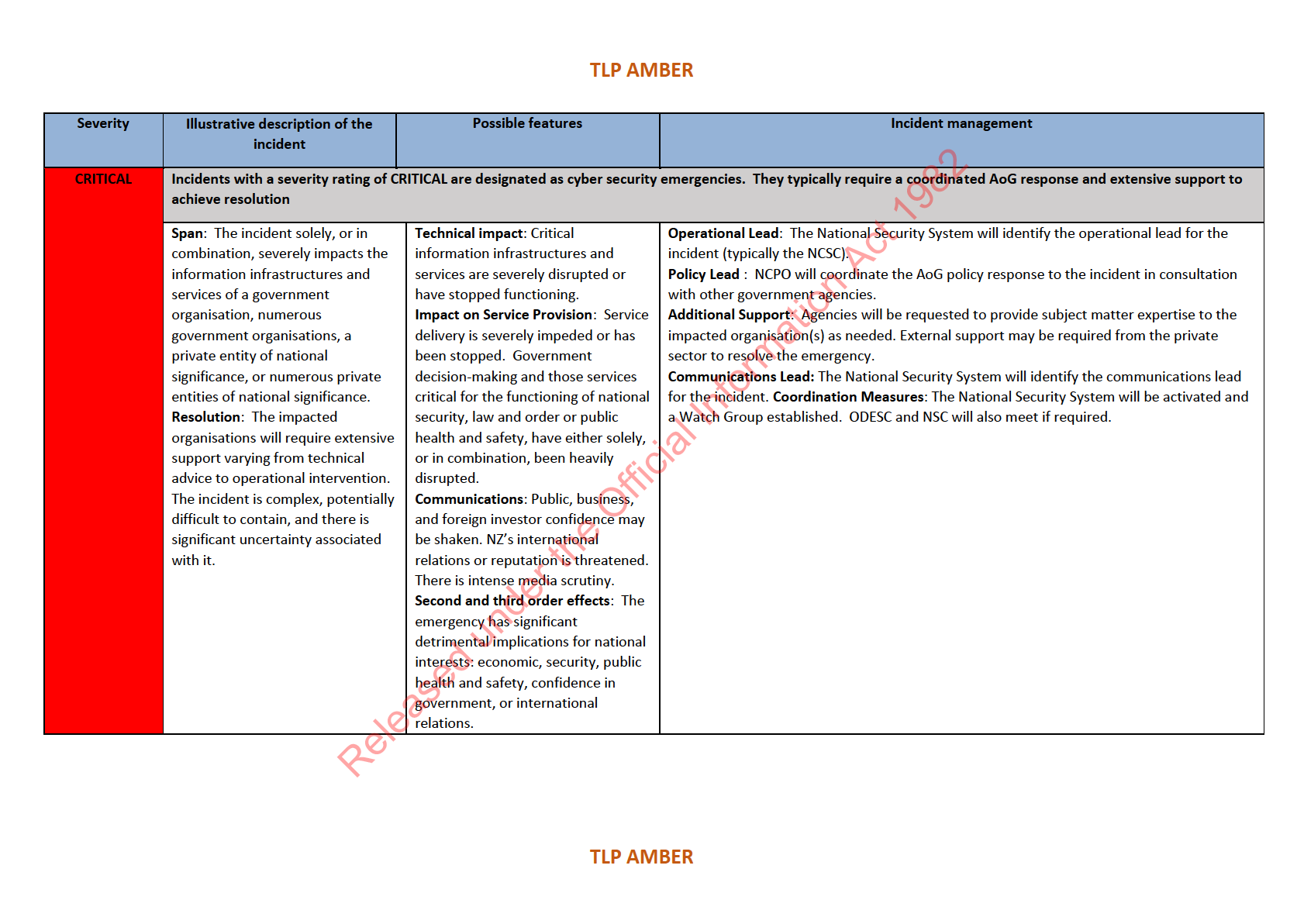
3 Definitions of these ratings can be found at Annex D, and are drawn from the National Cyber Security Emergency Response Plan.
TLP AMBER
TLP AMBER
Annex A
Organisation
Role
Tasks
m
f
lan
em
r o
n
ct
s
l
st
e
lic
r p
e
o
t
l
n
pa
to
egrity
na
ce fro
st
a
ub
n
na
ybe
int
an
ini
edi
ide
im
p
io
s
atio
ity Sy
ctivat
Z
m
se
ctivitie
at
N
a
r c
ist
cal
t
inc
u
nt
relatio
e a
N
em
to
cur
to
cto
ss
T N
ief M
th
o
t
lini
to
st
n
n
a
ER
ven
n
in
ine
l Se
e
o
se
/br
nd
o
Sy
io
ity Eve
ns
th
est
/C
th
r e
o
ify c
ng
r-crim
at
na
o
SC
ise
age wi
nt
di
al
io
ecisi
al
cisi
equ
C
dv
eal
esp
eterm
igital
at
esp
D
he
R
N
A
H
Eng
cybe
R
Ide
De
fun
cybe
D
D
Esc
Secur
N
R
CE(s) of affected
A A A2
A2
C A2 R2
C
C
C
health sector
entity(s) affected by
1982
cyber event [or
suitably
Act
empowered
delegate]
CIO/CISO/functional R1 R R2
I
R
I
C
C
R
R
ion
equivalent of health
at
sector entity
nt
affected by cyber
Information
event [or suitably
rese
empowered
p
delegate]
Re
CMO/functional
C
I
C
C
I
C
I
I
C
C
Official
tor
equivalent of health
sector entity
affected by cyber
the
th Sec
event [or suitably
empowered
Heal
delegate]
under
communications
I
I
I
R2
I
I
I
I
I
I
representative of
the health sector
entity(s) affected by
cyber event
Chair of DHB CIOs
Released
I
I
I
I
I
I
I
I
C
C
forum [or suitably
empowered
alternate]
incumbent Chair of
I
I
I
I
I
I
I
I
C
C
PHO CIOs forum [or
suitably
empowered
alternate]
TLP AMBER
TLP AMBER
incumbent Chair of
I
I
I
I
I
I
I
I
C
C
NGO Council [or
suitably
empowered
alternate]
legal representative
I
C
C
C
I
I
C
I
I
I
of the health sector
entity affected by
cyber event
Director-General of
I
I
A1
A1
C A1 R1
A A
A
Health [or suitably
empowered
delegate];
Deputy Director-
A
I
R1
C
C C
C
R
R
R
General (Data and
Digital)
Group Manager
C
C
C
C
C C
C
C
R
R
(Digital Strategy
and Investment) /
Group Manager
(National Digital
Services) [or
suitably
th
empowered
delegate]
Chief Security
R2 C
C
I
R
I
C
C
R
R
Advisor/
ry of Heal
Information
st
Technology Security
ni
Manager (National
Mi
Digital Services)
under the Official Information Act 1982
Director Emergency
I
I
C
I
R C
I
C
R
R
Management [or
current National
Health Coordination
Centre (NHCC) Duty
Officer]
Released
Chief Medical
C
I
C
C
I A1
I
I
C
C
Officer [or suitably
empowered
delegate]
Chief Privacy Officer
I
I
C
C
C
I
C
I
I
I
[or suitably
empowered
delegate]
TLP AMBER
TLP AMBER
Annex B
Criterion of a good cyber event response plan
When developing an internal cyber event response plan, the following components should
be included within it:
• analysis of the threat environment including the likelihood and severity of potential
incidents. Consider industry specific threats, the type and value of data you hold, third
party
networks
and
cyber
resilience
posture
of
your
networks;
• identification of key assets, data and critical systems. What are you working to protect
1982
and why does it need protecting?;
Act
• plans for each major incident type and different types of data that could be
compromised. For example, the theft of personnel data would have a very different
response to a ransomware attack. These plans should include timeframes and objectives;
• key roles and responsibilities of management and staff. It’s crucial all parties involved
understand the reporting lines—who will be making decisions, what the decision
thresholds are, what involvement there is from senior management, and when to
Information
engage with MoH and NCSC/CERT NZ;
• key tools including contact lists, checklists and guides for use during the response;
Official
• a process for alerting necessary stakeholders, including the Ministry of Health, and the
NCSC/CERT NZ, suppliers and external agencies that may be impacted;
the
• public relations and media management. What advice can you give your
customers/clients? Who is the media spokesperson and what can be said to the media?
If businesses fails to manage this well, the reputational damage can far outweigh the
under
actual business cost of the incident;
• arrangements to regularly review and exercise the plan. A plan might look good on paper
but it regularly needs to be exercised to ensure it is effective. Make sure there is a review
schedule that considers the frequency of changes to the organisation or the threat
Released
environment. For example - for a large organisation that has frequent structural changes
or new platforms, consider reviewing every three months. For a smaller organisation,
perhaps every six months; and
• post-incident review and reporting. It’s important to document the incident details and
response actions, collect the lessons learned and update the incident response plan to
improve future responses.
TLP AMBER
TLP AMBER
Other useful resources that can utilised in developing an effective cyber-event response
plan include:
➢ NCSC NZ – “The New Zealand Security Incident Management Guide for Computer
Security Incident Response Teams (CSIRTs);
➢ NIST – “Computer Security Incident Handling Guide”; and
➢ UK NHS Digital – “Information security incident: good practice guide“.
under the Official Information Act 1982
Released
TLP AMBER
TLP AMBER
Annex C
Key Health Sector Cyber Event Contacts
a. External technical guidance, assistance and support
National Cyber Security Centre
Ph: 04-498-7654,
E-mail: [email address]
CERT NZ
Ph: 0800-237-869,
URL: https://www.cert.govt.nz/it-specialists/report-an-incident/
b. MoH sector-wide cyber event response leads
Matthew Lord
Information Technology Security Manager
Data and Digital – Ministry of Health
Mobile: s 9(2)(a)
E-mail: [email address] nz or [email address]
under the Official Information Act 1982
Released
TLP AMBER