

 GCDO
Desktop-as-a-Service
(DaaS)
Risk Assessment Report
March 2022
Issued by
GCDO
Desktop-as-a-Service
(DaaS)
Risk Assessment Report
March 2022
Issued by
under the Official Information Act 1982
Digital Public Service Branch
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
IN-CONFIDENCE
Glossary of Terms
Availability
Ensuring that authorised users have timely and reliable access to
information.
API
A set of functions and procedures allowing the creation of
applications that access the features or data of an operating system,
application, or other service.
B2B
Business–to–business (B2B), also called B–to–B, is a form of
transaction between businesses.
Confidentiality
Ensuring that only authorised users can access information.
Consequence
The outcome of an event. The outcome can be positive or negative.
However, in the context of Information Security it is usually
negative.
Control
A risk treatment implemented to reduce the likelihood and/or
impact of a risk.
Gross Risk
The risk without any risk treatment applied.
Impact
See Consequence.
Information Security
Ensures that information is protected against unauthorised access
or disclosure users (confidentiality), unauthorised or improper
modification (integrity) and can be accessed when required
(availability).
Integrity
Ensuring the accuracy and completeness of information and
information processing methods.
Likelihood
See Probability.
NIST
The National Institute of Standards and Technology (NIST) is a
physical sciences laboratory and a non–regulatory agency of the
United States Department of Commerce. Its mission is to promote
innovation and industrial competitiveness.
Probability
The chance of an event occurring.
POC
A proof of concept (POC) is a demonstration to verify that certain
concepts or theories have the potential for real–world application.
Recovery Point Objective
The earliest point time that is acceptable to recover data from. The
(RPO)
RPO effectively specifies the amount of data loss that is acceptable
under the Official Information Act 1982
to the business.
Recovery Time Objective
The amount of time allowed for the recovery of an information
(RTO)
system or service after a disaster event has occurred. The RTO
effectively specifies the amount of time that is acceptable to the
business to be without the system.
Residual Risk
The risk remaining after the risk treatment has been applied.
Risk
The effect of uncertainty on the business objectives. The effect can
Released
be positive or negative. However, in the context of Information
Security it is usually negative.
GCDO DaaS Recertification Risk Assessment Report
Page 4 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Risk Appetite
The amount of risk that the organisation is willing to accept in
pursuit of its objectives.
Risk Owner
A person or entity with the accountability and authority to manage
a risk. Usually, the business owner of the information system or
service.
SRS Panel
The ICT Security and Related Services Panel (SRS Panel) are a group
of industry experts contracted to provide government agencies with
ICT services and advice on a range of security and privacy practices.
Stakeholder
A person or organisation that can affect, be affected by, or perceive
themselves to be affected by a risk eventuating.
Threat
A potential cause of a risk.
Vulnerability
A weakness in an information system or service that can be
exploited by a threat.
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 5 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Contents
Document Control
2
Document Information
2
Revision History
2
Document Approval
3
Executive Summary
7
Introduction
7
Key Risks
7
Gross Risks
10
Subscribing Agency Key Recommendations
11
Service Provider Key Recommendations
13
Residual Risks
14
Business Context
15
Certification Approach
15
Stakeholders
15
Information Classification
15
Business Processes Supported
16
Business Impact
16
Security Requirements
16
Users
18
Legislation, Policy and Guidelines
18
Information Protection Priorities
18
Detailed Risks
20
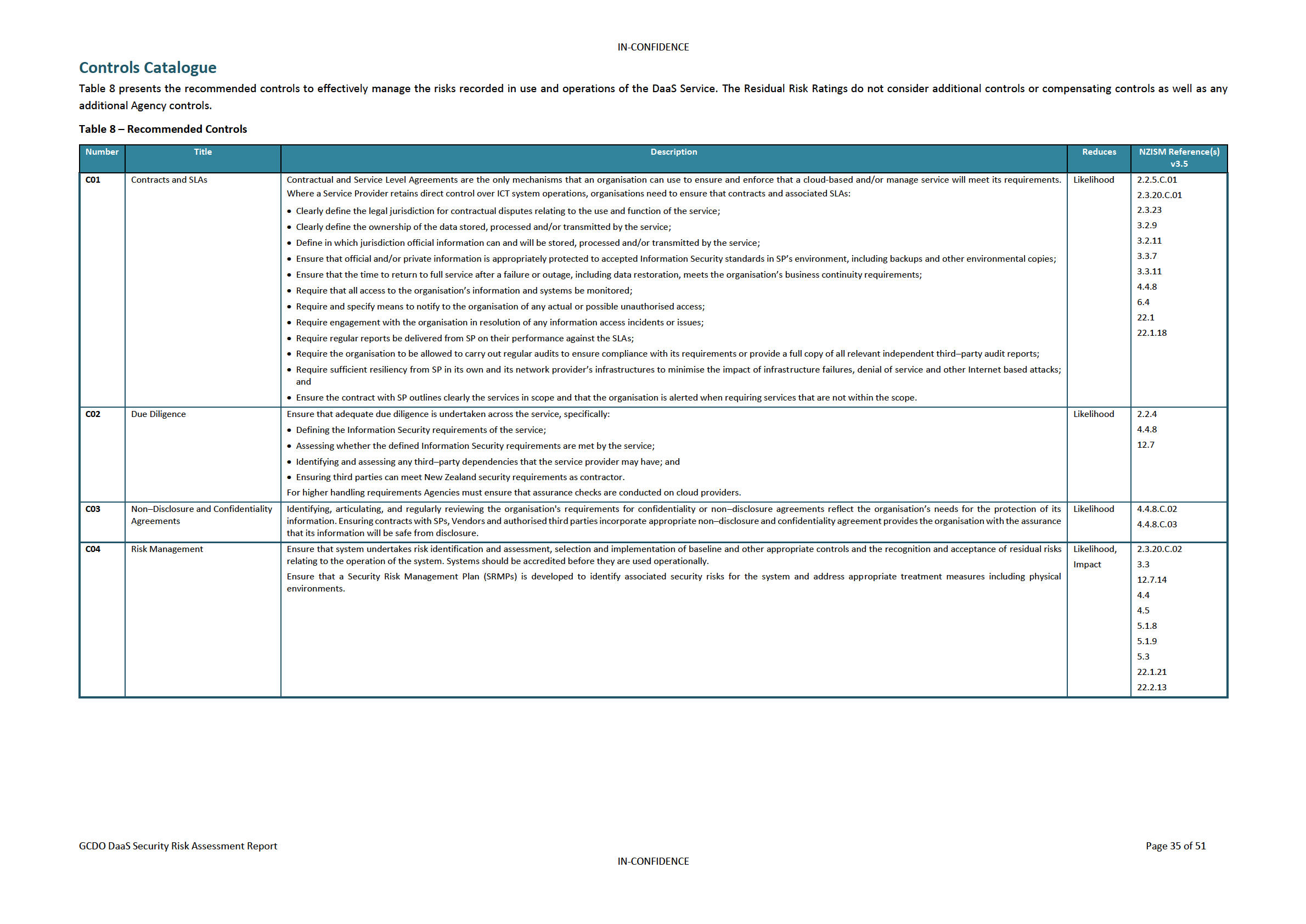
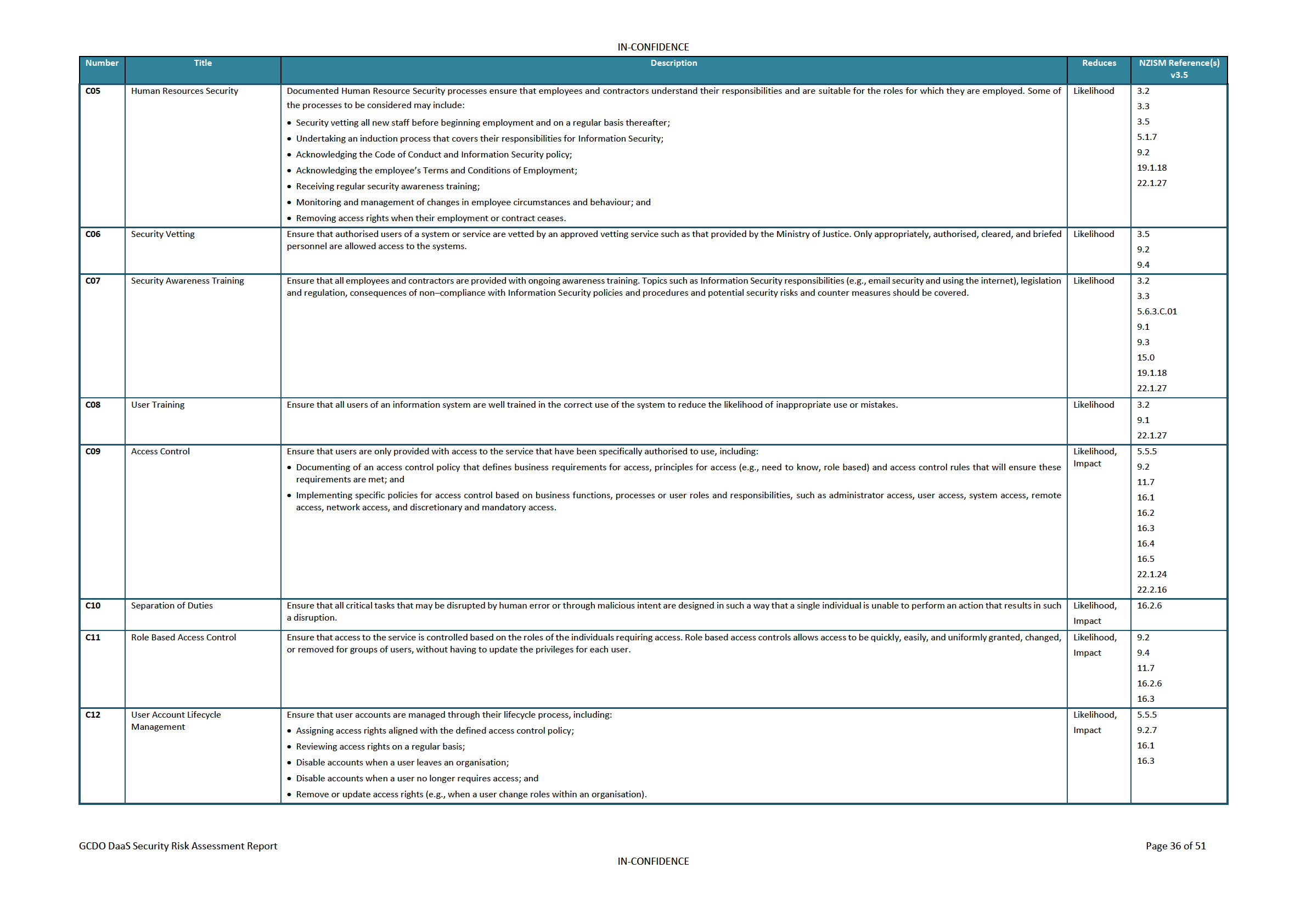
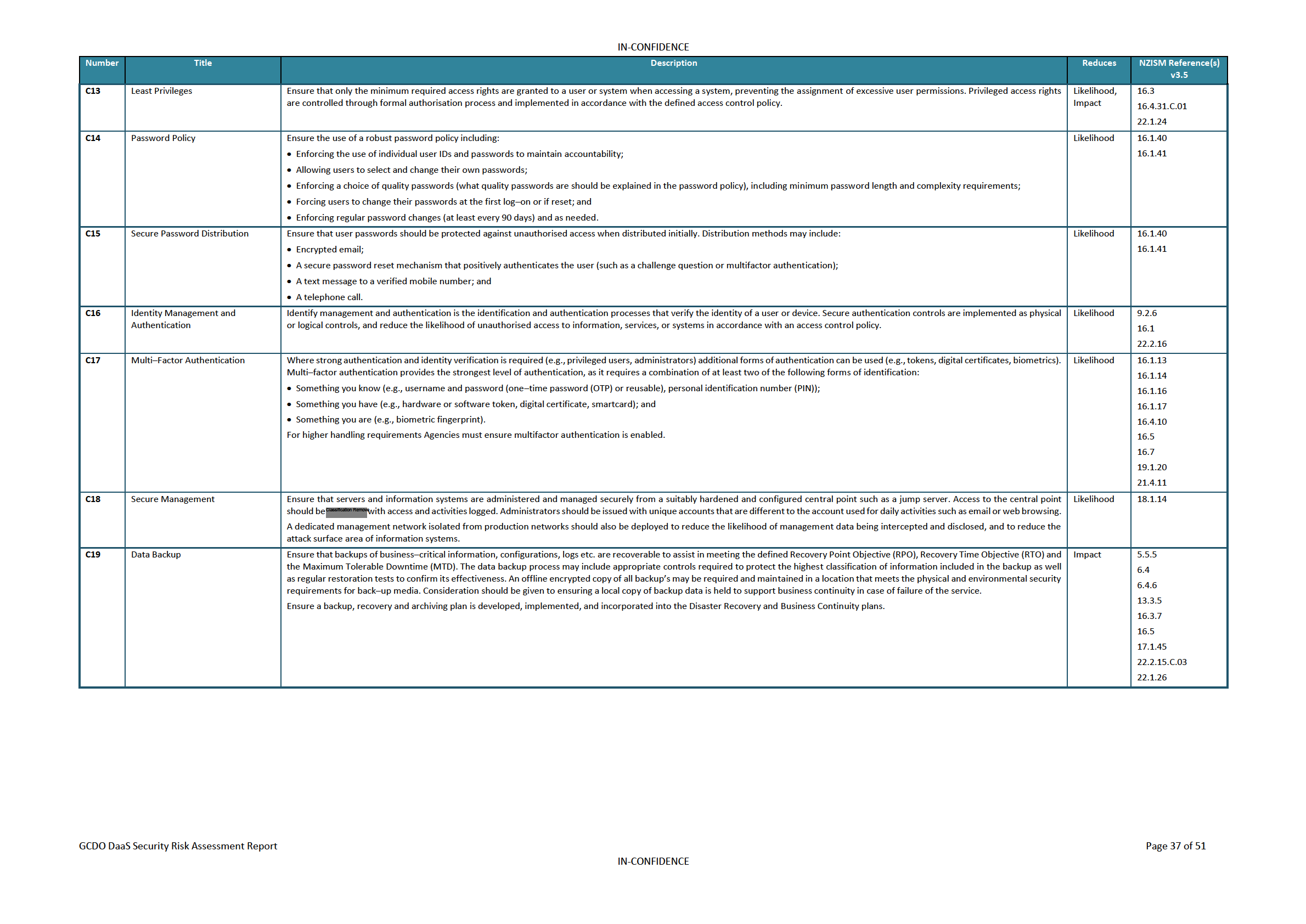
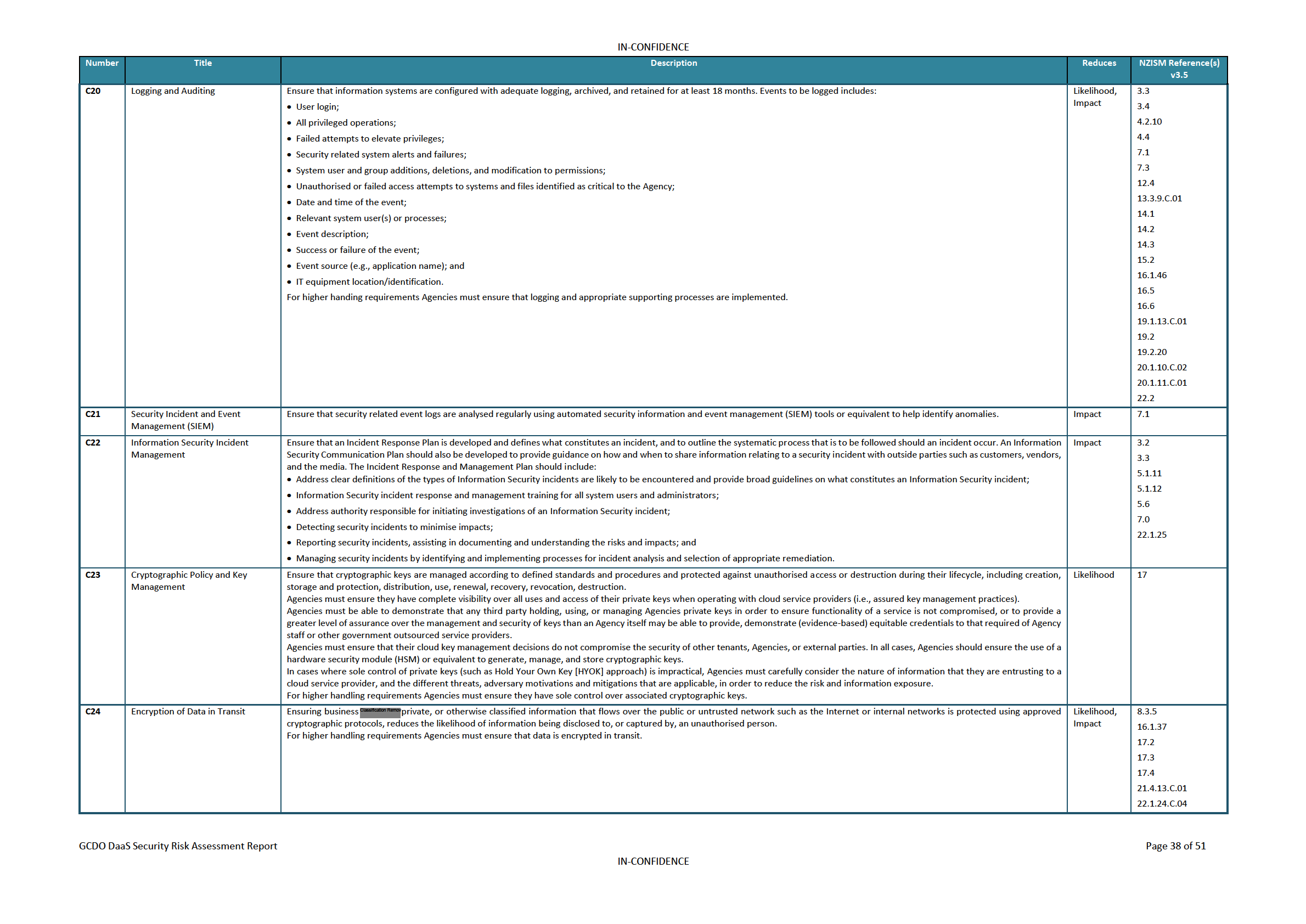
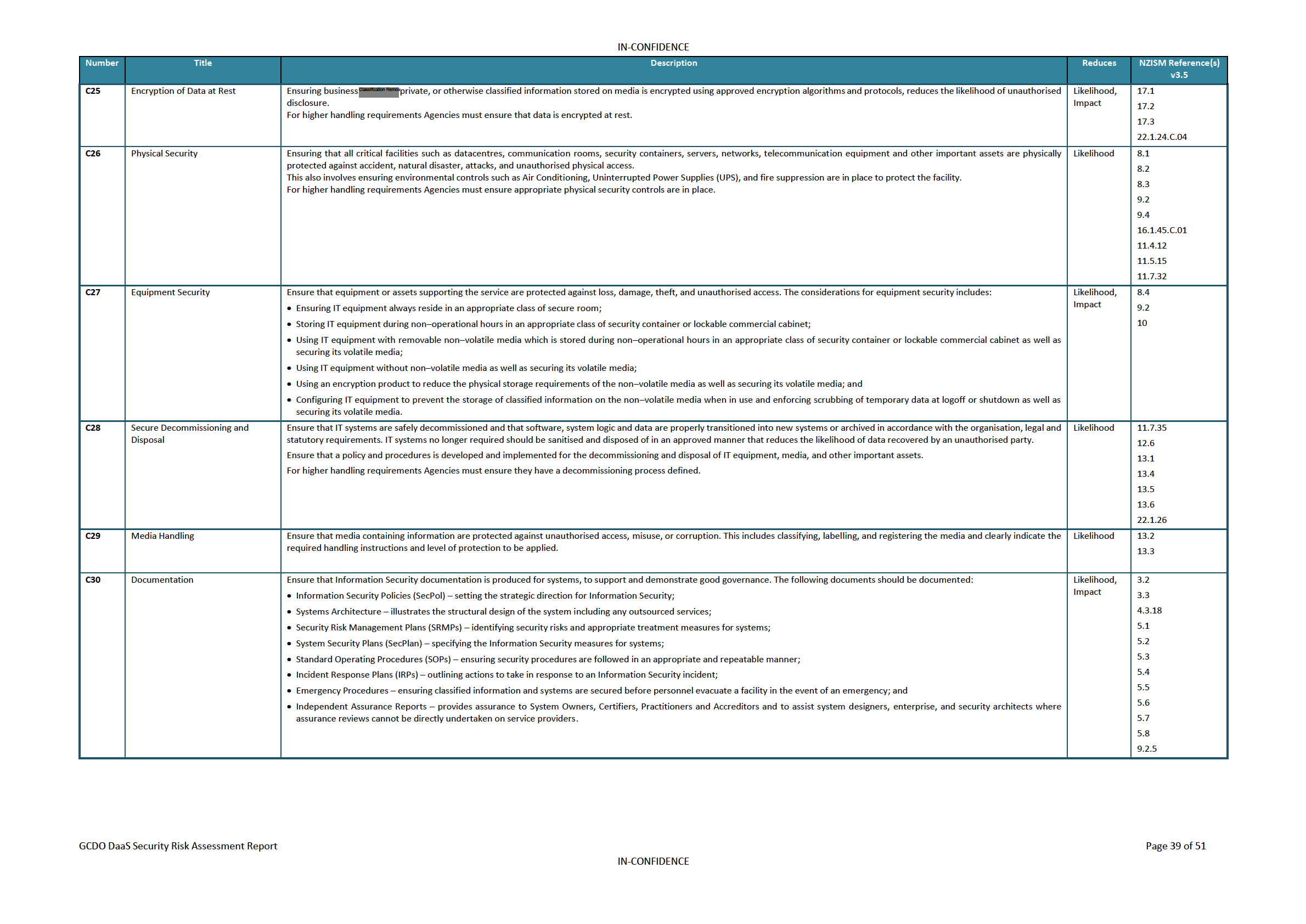
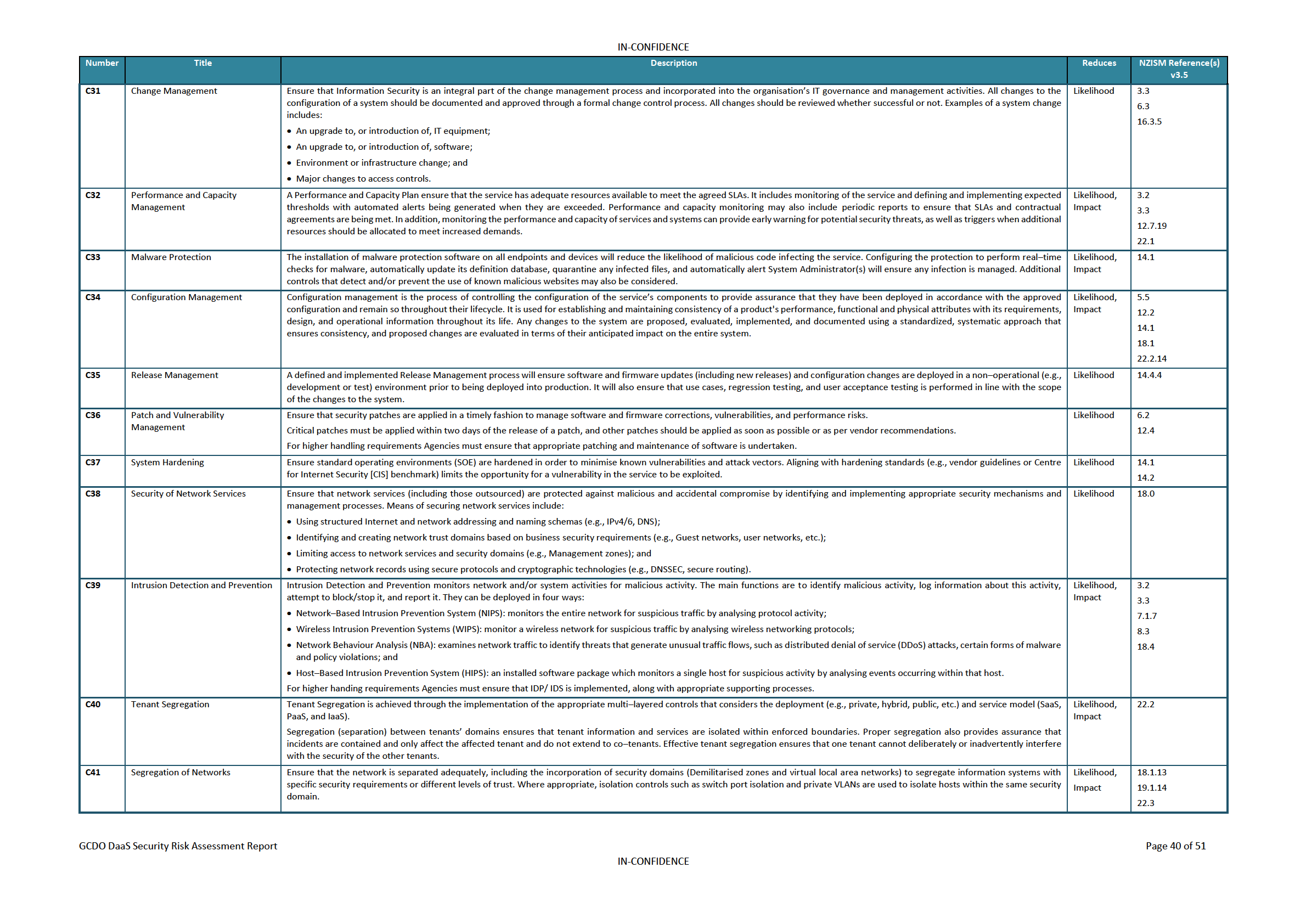
Controls Catalogue
35
Appendix A – Consulted Agencies
46
Appendix B – Project Overview
47
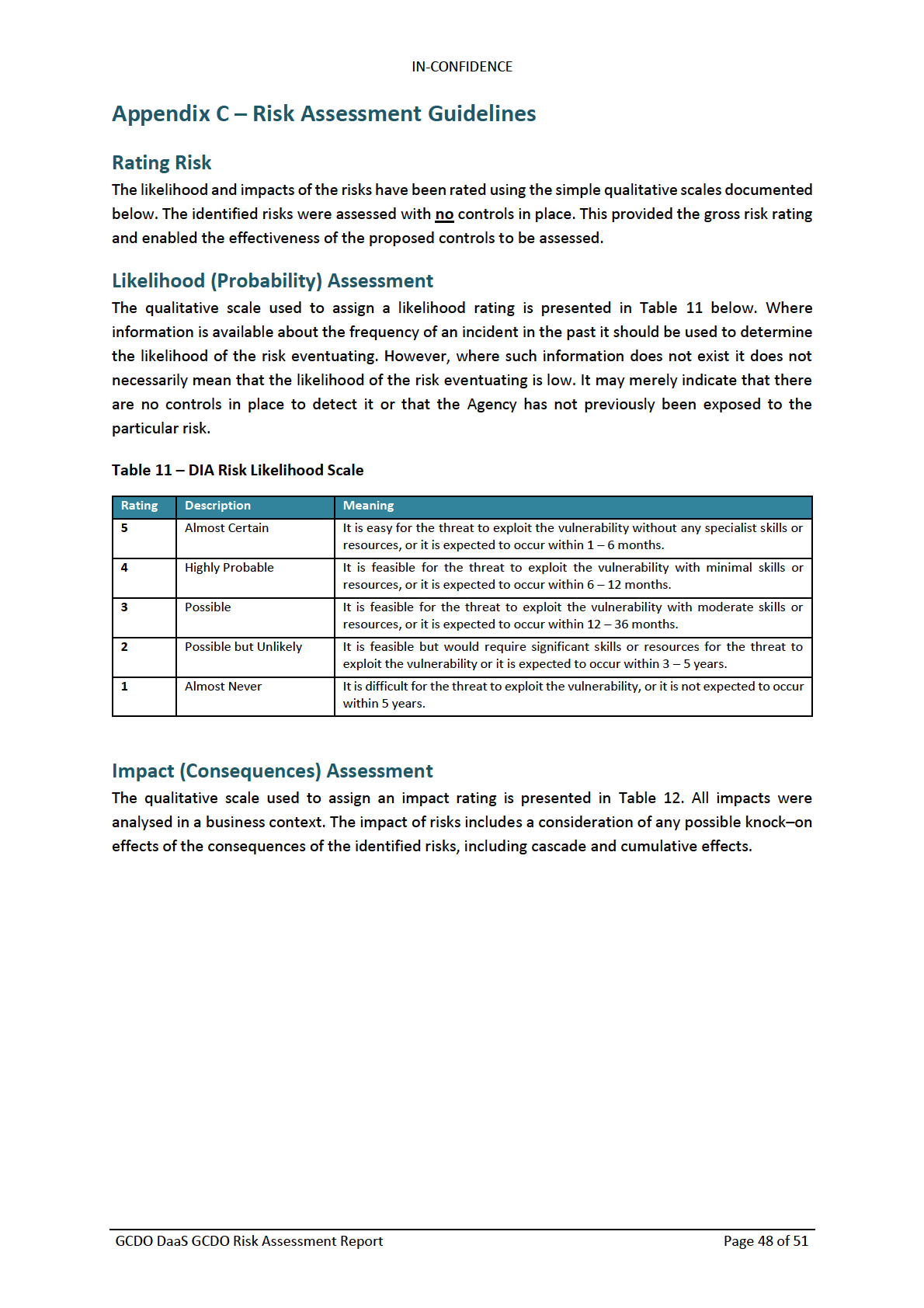
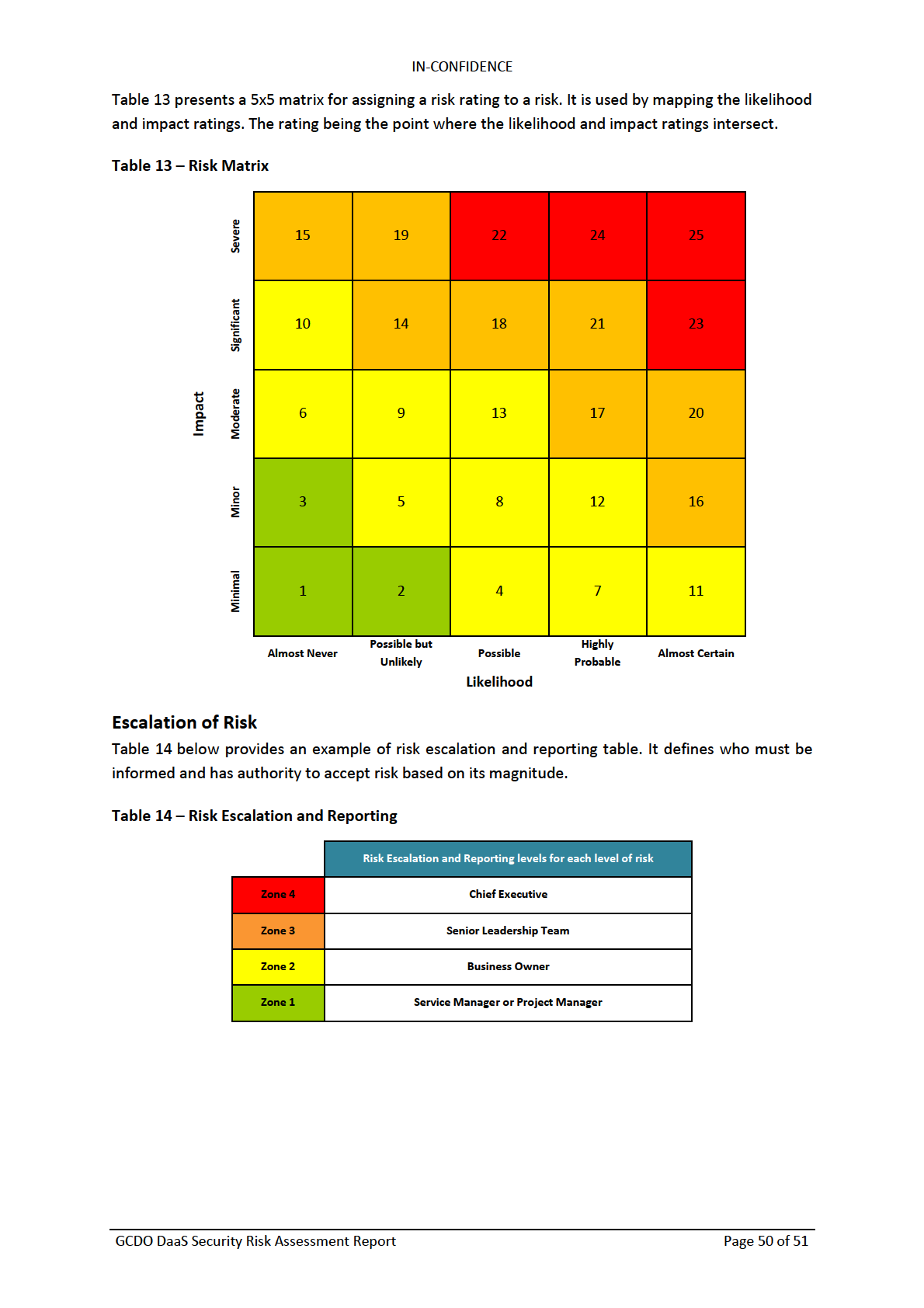
Appendix C – Risk Assessment Guidelines
48
Rating Risk
48
Likelihood (Probability) Assessment
48
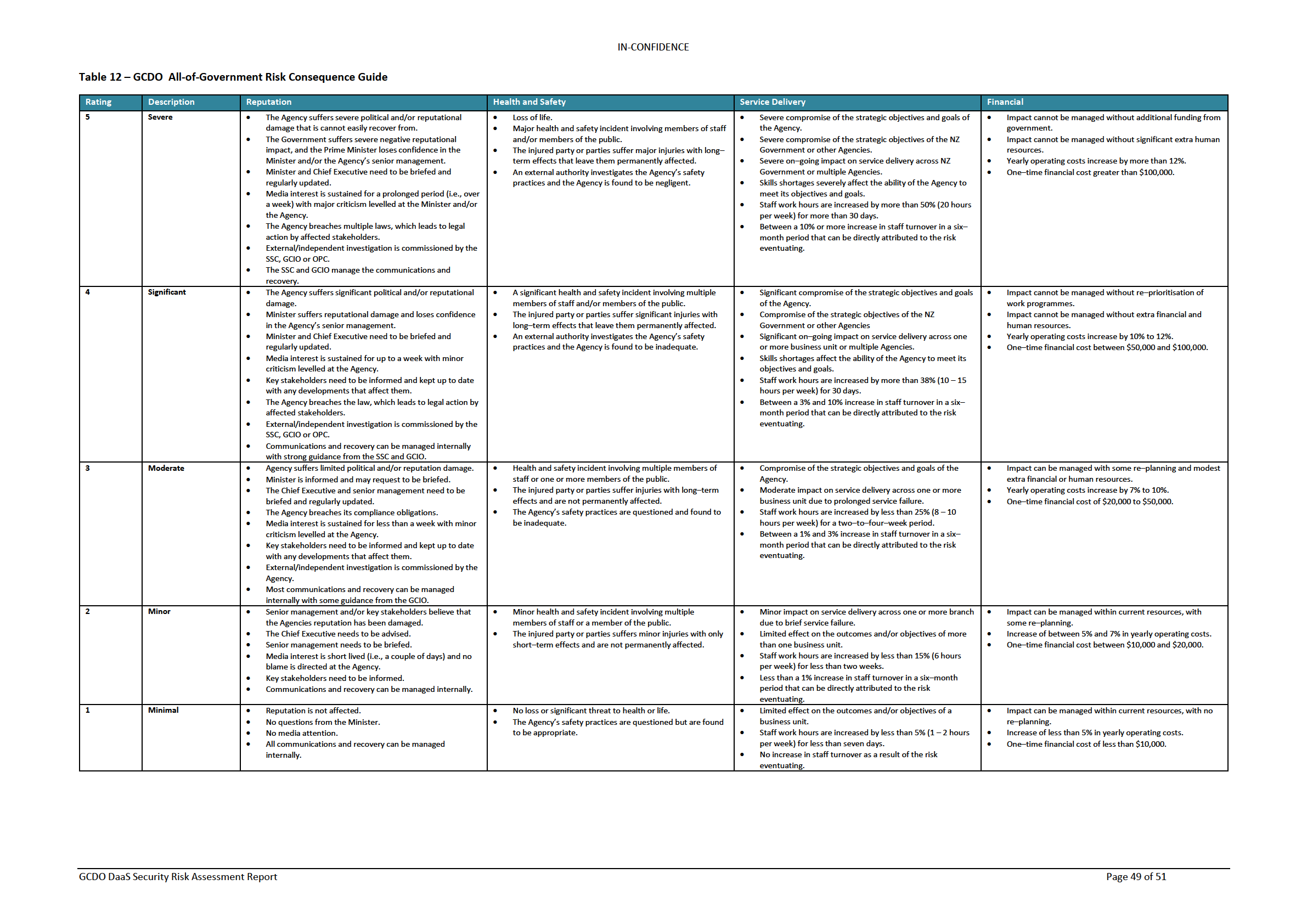
Impact (Consequences) Assessment
48
Appendix D – Controls and Considerations for Offshore Hosted Office Productivity Security
Requirements
51
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 6 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Executive Summary
Introduction
This report presents the findings of an Information Security Risk Assessment for the use and operation
of the Desktop-as-a-Service (DaaS) service by the All-of-Government (AoG) Service Delivery (SD)
business group of the Department of Internal Affairs (DIA)’s Digital Public Service (DPS) branch. The
Risk Assessment followed the Government Chief Digital Officer’s (GCDO) Risk Assessment process,
which is based on the AS/NZS ISO 31000:2009 and ISO/IEC 27005:2011 risk management standards.
As this is a generic Information Security Risk Assessment report, the risks identified, and ratings
assessed may be different and unique in the context of Subscribing Agencies (SAs) and the DaaS
service being consumed. Therefore, agencies reading this report should review the risks using their
own risk management framework. This ensures that the risks identified are specific to the agency’s
adoption of DaaS, are within their business context, and risk appetite.
It should be noted that this Information Security Risk Assessment only identifies risks related to the
operations of the DaaS service. The information security risks associated with the DaaS service were
previously assessed in 2016. Therefore, the approach taken in preparing this updated risk assessment
was to use the previous assessment as a base and then consider:
1. Has anything changed in the environment or threat landscape that may affect the risk profile?
2. Are the previously identified risks and their controls still valid/relevant?
3. What is current good practice to ensure the products are safe, secure, and resilient?
4. Does DaaS align with Deputy Chief Executive (DCE) and General Manager (GM) priorities?
5. Have any new dependencies on the DaaS service come to light that may affect the risk profile?
Where
SA and
SP are used in this report, they refer to
Subscribing Agency (SA) and
DaaS Service
Provider (SP) respectively.
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 7 of 51
IN-CONFIDENCE
IN-CONFIDENCE
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 8 of 51
IN-CONFIDENCE
IN-CONFIDENCE
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 9 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Gross Risks
Table 1 illustrates the rating of each risk without any controls in place.
Table 1 – Gross Risk Ratings
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 10 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Subscribing Agency Key Recommendations
The Risk Assessment included key controls that if implemented, helps to address the identified risks.
A controls validation plan (CVP) was also developed to specify the recommended controls outlined in
the Risk Assessment. The CVP has been detailed in the
GCDO Certification for Agencies Consuming
DaaS, within section
6.1 Controls Validation Plan.
9(2)(k)
To mitigate and manage the identified gross risks rated
9(2)(k)
the following key recommendations should be undertaken. The following
recommendations can be undertaken by the SA.
1. Due Diligence
Before the consumption of the DaaS service, agencies should be informed and aware of the
implicating risks associated with using the service. This can be done by performing a
comprehensive Risk Assessment to identify the risks and controls associated with the service. It
may also involve conducting a data impact assessment, privacy assessment, or jurisdictional Risk
Assessment depending on the types of data to be stored. All identified risks should be understood
and formally accepted with an appropriate risk management plan by the SA before consuming
DaaS.
The amount of due diligence performed should also extend to aspects related to supply chain risks
and the ability to obtain appropriate security assurance from the supplier.
2. Contracts and Service Level Agreements (SLAs)
DaaS agreements should define the agency’s requirements for the service to ensure it is met by
the DaaS SP. This should include the DaaS SP terms of service, associated SLAs, key performance
indicators, and metric demonstrating service performance.
Regular monitoring of the DaaS SP service performance should be carried out to ensure that
expectations are continuously met. This includes any third parties contracted by the DaaS SP to
provide services supporting DaaS.
3. Use of Strong Encryption
The use of strong encryption algorithms to protect data in transit and at rest is a key control to
address confidentiality risks within the cloud.
Agencies should ensure that all requirements around protecting data in transit and at rest are well
defined and included in contracts or SLAs, specifically for data backups and data in transit across
untrusted networks.
under the Official Information Act 1982
4. Access Controls
Ensure the identification, implementation and ongoing effectiveness of access controls is
maintained. Specific policies for access control should be implemented based on business
functions, processes, or user roles and responsibilities. User accounts should be managed through
their lifecycle, ensuring that only the minimum required access rights are granted, preventing the
assignment of excessive user permissions. Privileged access should be controlled through a formal
authorisation process and implemented in accordance with the defined access control policy.
Released
Ensure the use of a robust password policy and implement multi-factor authentication where
GCDO DaaS Recertification Risk Assessment Report
Page 11 of 51
IN-CONFIDENCE
IN-CONFIDENCE
possible. IP whitelisting should be used to limit and control access to trusted users and locations
only.
5. User Awareness and Training
SA DaaS users should be provided with robust role-based training and have access to Standard
Operating Procedures for essential tasks required by their role. All staff should also receive
training in security practices to prevent social engineering attacks, ensure that unescorted visitors
are challenged and that potential security incidents are detected and reported appropriately.
6. Incident Management and Response
Effective incident management procedures are essential for the detection and resolution of
security incidents. Response procedures should be formally documented, approved, and reviewed
to be implemented and maintained effectively. Incident response training should be provided to
staff, and response plans should be tested on a regular basis. Effective implementation of this risk
will reduce the impact of security incidents, and the timeliness of resolution.
The presence of adequate logging and regular monitoring of the DaaS environment can help the
SA detect or investigate security incidents associated with DaaS should they occur. This includes
enabling sufficient logging and monitoring on the DaaS infrastructure and virtual desktop
applications.
under the Official Information Act 1982
Released
GCDO DaaS Recertification Risk Assessment Report
Page 12 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Service Provider Key Recommendations
9(2)(k)
To mitigate and manage the identified gross risks rated
9(2)(k)
the following key recommendations should be undertaken. The following key
recommendations can be undertaken by SPs.
1. Supply Chain Management
SPs should ensure robust supply chain management processes are in place to reduce the likelihood
and impact of an issue with one of their providers. A robust supply chain monitoring may include
conducting Risk Assessments on providers, conducting audits, ensuring robust change
management is in place for introducing new vendors and technologies, and monitoring the cyber
threat landscape.
2. Use of Strong Encryption
SPs should ensure the use of strong encryption algorithms to protect data in transit and at rest in
accordance with requirements defined in contracts or SLAs or in line with industry best practice.
3. Access Controls
Robust access controls within a SP environment are needed to ensure that only those who require
access can access resources. SP must ensure that the principal of least privilege is used within their
environment, as well as regular access reviews and robust logging of administrator actions.
Ensuring strong password policies are enforced and enforcing Multi-Factor Authentication (MFA)
for all actions reduces the likelihood for compromise.
4. User Awareness and Training
DaaS SP users and third parties should be provided with robust role-based training and have
access to Standard Operating Procedures for essential tasks required by their role. All staff should
also receive training in security practices to prevent social engineering attacks, ensure that
unescorted visitors are challenged and that potential security incidents are detected and reported
appropriately.
5. Configuration and Vulnerability Management of DaaS Virtualisation Platform
Change and vulnerability management procedures should be well defined and followed to ensure
that the risks associated with misconfigurations and vulnerabilities that affect DaaS are addressed
and mitigated, in particular to ensure muti-tenant segregation.
A robust vulnerability management process should be followed. This includes regular vulnerability
assessments, software patching and updating.
under the Official Information Act 1982
6. Physical Security Controls
SPs must ensure that appropriate physical security controls are applied to their environment to
ensure resources are well protected, and SA data is kept secure. Conducting physical security
reviews on datacentres will assist in ensuring that they are protected from accidents, natural
disasters, attacks, and unauthorised physical access. They will also ensure that there are
appropriate protections in place such as fire suppression if an issue were to occur.
Released
GCDO DaaS Recertification Risk Assessment Report
Page 13 of 51
IN-CONFIDENCE
IN-CONFIDENCE
Residual Risks
The tables below illustrate the expected residual rating of each of the risks if all the recommended controls are implemented and appropriately configured and managed.
9(2)(k)
under the Official Information Act 1982
GCDO DaaS Security Risk Assessment Report
Page 14 of 51
IN-CONFIDENCE
Released
IN-CONFIDENCE
Business Context
This section provides an overview of the generic business context for the DaaS services that are in
scope of this Security Risk Assessment.
Certification Approach
The following business context assumptions have been made for the Risk Assessment, with input from
a sample of Agencies:
• DaaS models and shared security responsibility;
• Key stakeholders involved in consuming the DaaS;
• Classification of the information stored, processed, and transmitted by the DaaS;
• Different types of users with access to the DaaS;
• Information Security requirements for DaaS in terms of confidentiality, integrity, availability,
privacy, and any other relevant legislation; and
• Information protection priorities for the DaaS.
Subscribing agencies consuming the Risk Assessment must ensure that they:
• Review the business context assumptions made during the Risk Assessment and ensure that
they accurately reflect the agency’s own context;
• Define the business process that will be supported by the DaaS service;
• Identify and document the business impact should an Information Security or Privacy incident
occur; and
• Consider the agency’s use context and risk appetite and evaluate assigned risk ratings.
Stakeholders
The following stakeholders for DaaS have been identified:
• The DIA AoG SD team of the DPS branch;
• Subscribing Agency (SA) Business Owner; and
• SA Technical Owner.
Information Classification
Based on the New Zealand Government Security Classification System1, the information that will be
under the Official Information Act 1982
stored, processed, or transmitted by the DaaS service has been classified Classification Removedand below. The
compromise of information classified as Classification Removed and below can:
• Adversely affect diplomatic relations;
• Hinder the operational effectiveness or security of New Zealand or friendly forces;
• Adversely affect the internal stability or economic wellbeing of New Zealand or friendly
countries;
Released
1 https://www.protectivesecurity.govt.nz/information-security/classification-system-and-handling-
requirements/classification-system/national-security-information/
GCDO DaaS Security Risk Assessment Report
Page 15 of 51
IN-CONFIDENCE
IN-CONFIDENCE
• Prejudice the maintenance of law, including the prevention, investigation and detection of
offences, and the right to a fair trial;
• Affect adversely the privacy of natural persons, including that of deceased natural persons;
• Impede government negotiations (including commercial and industrial negotiations);
• Disclose a trade secret or unreasonably to prejudice the commercial position of the person
who supplied or is the subject of the information;
• Endanger the safety of any person;
• Prejudice measures protecting the health or safety of members of the public;
• Prejudice measures that prevent or mitigate material loss to members of the public;
• Breach legal professional privilege;
• Impede a Minister of the Crown or any Department or organisation holding the information
to carry out, without prejudice or disadvantage, commercial activities; and
• Lead to the disclosure or use of official information for improper gain or advantage.
Business Processes Supported
DaaS delivers a managed virtual desktop environment for the use of New Zealand government
agencies. DaaS enables agency staff to access their desktop operating system and desktop applications
in a more efficient manner, as well as the flexibility for agencies to scale up or back service use and
costs as required.
The DaaS service is integrated with the agency’s existing IT infrastructure and delivered from within
an approved government Infrastructure-as-a-Service (IaaS) datacentre.
Business Impact
This section describes the business impact as it would apply to a SA should the confidentiality,
integrity, availability, or privacy of the information stored, processed, or transmitted by the DaaS
service be compromised.
Impacts may be different and unique for different SAs. Therefore, a SA must consider its own
objectives and context when considering the consequences should a risk be realised.
Security Requirements
under the Official Information Act 1982
The Confidentiality, Integrity and Availability requirements for DaaS have been defined as follows:
Confidentiality
The confidentiality of the information transmitted, stored, or processed by DaaS is considered as
4 –
Highly-Important. This is largely driven by the Classification Removed classification of information that will be
transmitted, stored, or processed by DaaS.
If the confidentiality of information was compromised, the following impacts are expected:
•
Released
Classification Removed information is disclosed to unauthorised parties;
• The affected SA’s reputation is damaged;
• The strategic objectives of the New Zealand Government are compromised;
GCDO DaaS Security Risk Assessment Report
Page 16 of 51
IN-CONFIDENCE
IN-CONFIDENCE
• Loss of confidence by the stakeholders and Portfolio Ministers; and
• Increased workload for DIA and other Lead Agency staff to solve the security incident.
Integrity
The integrity of the information transmitted, stored, or processed by DaaS is considered as
4 –
Highly-Important. The DaaS information contained within its virtualised desktop environment
must be stored and transmitted in a secure manner to prevent it from being modified by an
unauthorised person. Inaccurate or corrupted information can cause the SA to lose their data source
of truth. The SA is then unable to rely on the DaaS environment and this will affect business operations.
If the integrity of information was compromised, the following impacts are expected:
• Government decisions are misinformed;
• The affected SA’s reputation is damaged;
• The strategic objectives of the New Zealand Government are compromised;
• Loss of confidence by the stakeholders and Portfolio Ministers;
• Increased workload for DIA and other Lead Agency staff to solve the security incident; and
• Increased workload for DIA and other Lead Agency staff to assess the accuracy of the
information and provide corrective actions.
Availability
The service availability requirement for DaaS is defined as 24/7 at 99.9% availability. If the availability
of the DaaS service was compromised, the business impact would be
4 – Highly-Important. The
following consequences are expected:
• Agency users may not be able to access the service;
• Lead Agencies’ users may not be able to access the service;
• Data may not be accessible;
• Government Strategic decisions may be delayed;
• Increased workload for Agency and Lead Agency users as they rely on manual failback
processes;
• Increased workload for DIA staff to solve the security incident; and
• Loss of confidence by the stakeholders.
Privacy
under the Official Information Act 1982
Personally Identifiable Information (PII) may be included in the DaaS virtual desktop environment. It
is highly important that the privacy of the information is adequately protected from unauthorised
disclosure or modification during storage and in transit.
If the privacy of the DaaS service was compromised, the business impact will be
4 – Highly-Important.
The following consequences are expected:
• Disclosure of personal information to unauthorised parties, resulting in a privacy breach;
•
Released
Loss of key stakeholder confidence in DaaS service;
• Reputation damage for the affected SA; and
• Further investigation where required by law.
GCDO DaaS Security Risk Assessment Report
Page 17 of 51
IN-CONFIDENCE
under the Official Information Act 1982
Released

under the Official Information Act 1982
Released
under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released

under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
IN-CONFIDENCE
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS GCDO Risk Assessment Report
Page 44 of 51
9(2)(k)
under the Official Information Act 1982
Released
GCDO DaaS GCDO Risk Assessment Report
Page 45 of 51
under the Official Information Act 1982
Released
IN-CONFIDENCE
Appendix B – Project Overview
Scope
The Department of Internal Affairs (DIA), as Government Chief Digital Officer (GCDO) have written this
Risk Assessment report and Controls Validation Plan (CVP) for service providers, for the use of
Desktop-as-a-Service (DaaS) by Subscribing Agencies. The objective was to create a generic Risk
Assessment and Controls Validation Plan (CVP) for the use of DaaS by Subscribing Agencies. The CVP
has been detailed in the
GCDO Certification for Agencies Consuming DaaS, within section
6.1 Controls
Validation Plan.
Approach
The Risk Assessment followed the GCDO risk framework based on the AS/NZS ISO 31000:2009 and
ISO/IEC 27005:2011 risk management standards. The assessment was conducted as a series of
workshops and document reviews, including:
• Consumption of documentation provided by DIA.
• Identification of risks and controls associated with the use of DaaS Services.
• Development of a Risk Assessment report in draft.
• Running workshops with Subscribing Agencies.
• Issuance of a final Risk Assessment report.
Documents Referenced
The following documentation were referenced and used to inform the Risk Assessment:
• All of Government Cloud Computing: Information Security and Privacy Considerations April
2014.
• DaaS Risk Assessment Report, v1.1, 10/11/2016.
under the Official Information Act 1982
Released
GCDO DaaS GCDO Risk Assessment Report
Page 47 of 51
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
under the Official Information Act 1982
Released
IN-CONFIDENCE
Appendix D – Controls and Considerations for Offshore Hosted Office
Productivity Security Requirements
GCDO/GCSB guidance on Security Controls for Hosted Offshore Office Productivity Services4 identifies
baseline controls that Agencies needs to address to ensure compliance of relevant controls from the
NZISM. Although not specifically targeted at addressing DaaS services, the controls identified in this
document are directly applicable where Agencies need to address higher levels of handling
requirements (i.e., Classification Removed
). Where appropriate, the controls below have been
incorporated into this Risk Assessment to maintain alignment.
The following list outlines recommendations Agencies should be aware of in the consumption of the
Public Cloud service:
• No material classified at CONFIDENTIAL and above can be stored in offshore office
productivity services;
• Agencies must ensure that data is encrypted in transit and at rest;
• Agencies must have sole control over associated cryptographic keys;
• Agencies must ensure that multi-factor authentication is used to control access to the service;
• Agencies must have decommissioning processes as outlined in the NZISM;
• Agencies must ensure that there are appropriate security controls over physical access to
Datacentres;
• Agencies must have assurance checks on cloud service providers in accordance with the
NZISM;
• Agencies must have controls over the interaction between Public Cloud services and end user
devices;
• Agencies must have assurance that appropriate patching and maintenance of software is
undertaken;
• Agencies must have process controls relating to intrusion detection, investigations, and
enterprise logging;
• Agencies must ensure compatibility with existing government security technology services
such as Classification
a
Remove
nd, where appropriate, cyber defence capabilities;
• Agencies must ensure there are technical protections to prevent data-mingling on shared
storage platforms;
• Where necessary, re-architect Agency ICT networks to ensure that cloud services can be used
safely and effectively; and
under the Official Information Act 1982
• Agency must revise their Agency disaster-recovery plans to cater for cloud-based services.
Released
4 https://snapshot.ict.govt.nz/resources/digital-ict-archive/static/localhost 8000/assets/Uploads/Security-
Requirements-for-OH-Office-Productivity-Jan-2017.pdf
GCDO DaaS Security Risk Assessment Report
Page 51 of 51


































