Stats NZ Internal Audit
Stats NZ Internal Audit
Stats NZ Internal Audit
Identity and Access Management Strategy and Roadmap
Author:
Date: 2 May 2017
Version 1.0
COMMERCIAL IN CONFIDENCE
Page 1 of 41
Stats NZ Internal Audit
TABLE OF CONTENTS
1
INTRODUCTION .............................................................................................................5
2
EXECUTIVE SUMMARY .....................................................................................................6
2.1 Background .................................................................................................................................... 6
2.2 Engagement Objectives ................................................................................................................. 6
2.3 Findings .......................................................................................................................................... 6
2.4 Recommendations ......................................................................................................................... 6
3
FUTURE STATE REQUIREMENTS ..........................................................................................8
3.1 High-Level Future Capabilities Required of IAM ............................................................................ 8
3.1.1
User Roles and Attributes ............................................................................................... 8
3.1.2
Identity Lifecycle Management ...................................................................................... 8
3.1.3
Access Control ................................................................................................................ 8
3.1.4
Monitoring and Audit ..................................................................................................... 9
4
CURRENT STATE .......................................................................................................... 10
4.1 Personas .......................................................................................................................................10
4.1.1
STATS Employees ..........................................................................................................10
4.1.2
Contractors, Other Agencies Staff and Industry partners ............................................10
4.1.3
IDI Researchers .............................................................................................................10
4.1.4
Census Staff ..................................................................................................................10
4.1.5
Citizens ..........................................................................................................................11
4.2 Current State Identity Management Components ......................................................................11
4.2.1
PSE ................................................................................................................................11
4.2.2
Novel IDM .....................................................................................................................11
4.2.3
QuestOne Active Roles .................................................................................................11
4.2.4
Lotus Notes ...................................................................................................................11
4.2.5
Active Directory (STATS) ...............................................................................................11
4.2.6
Active Directory (IDI) ....................................................................................................12
4.2.7
Azure Active Directory ..................................................................................................12
4.2.8
AADConnect ..................................................................................................................12
4.2.9
Salesforce ......................................................................................................................12
4.2.10 Cherwell ........................................................................................................................12
4.3 Current State Identity Management Process ..............................................................................14
4.3.1
Provisioning ..................................................................................................................14
4.3.2
User Lifecycle Changes .................................................................................................17
4.3.3
De-Provisioning .............................................................................................................17
4.4 Current State Access Management..............................................................................................18
4.5 Current State Audit and Control ..................................................................................................21
4.6 Current State Data Classification .................................................................................................21
4.7 Current State Externally Available Data .......................................................................................21
4.8 Current State Capabilities ............................................................................................................21
4.8.1
User Roles and Attributes .............................................................................................22
4.8.2
Identity Lifecycle Management ....................................................................................22
4.8.3
Access Control ..............................................................................................................23
4.8.4
Monitoring and Audit ...................................................................................................23
4.1 Current State Identity and Access Management Summary .........................................................23
4.1.1
Current State Concerns and Constraints ......................................................................24
COMMERCIAL IN CONFIDENCE
Page 3 of 41
Stats NZ Internal Audit
5
RECOMMENDATIONS .................................................................................................... 25
5.1 Communicate an Agreed Organisational Identity and Access Management Strategy ................25
5.2 Complete Analysis and Requirements Gathering to Inform IDAM Decision Making ..................25
5.3 Develop and communicate an agreed future state architecture ................................................25
5.3.1
Develop and Apply Appropriate Service Ownership and Process ................................25
5.3.2
Centralise and Automate the Provisioning and Management of Identity ...................26
5.3.3
Implement Role Based and Attribute Based Access Controls ......................................26
5.3.4
Implement Federation for Cloud Access Control .........................................................27
5.3.5
Implement User Self-Service ........................................................................................27
5.3.6
Implement Self-Service Password Reset ......................................................................27
5.3.7
Implement Multi-Factor Authentication ......................................................................28
5.3.8
Implement Privileged Access Management .................................................................28
5.3.9
Implement Monitoring and Audit functionality ...........................................................28
5.3.10 Minimise the Impact of Census Staff Management .....................................................28
5.4 Quick Wins ...................................................................................................................................29
5.4.1
Synchronise Accounts To Azure Active Directory .........................................................29
5.4.2
Implement Cloud App Security – Discovery .................................................................29
5.4.3
Implement Advanced Threat Analytics.........................................................................29
6
FUTURE STATE REFERENCE ARCHITECTURE .......................................................................... 30
6.1 Future State Reference Architecture Overview ...........................................................................31
6.1.1
Identity Provisioning and Lifecycle Management Service ............................................31
6.1.2
Attribute Sources ..........................................................................................................31
6.1.3
On-Premise Access Control ..........................................................................................31
6.1.4
IDI Environment ............................................................................................................31
6.1.5
Microsoft Azure Services ..............................................................................................31
6.2 Future State Capabilities ..............................................................................................................34
6.2.1
User Roles and Attributes .............................................................................................34
6.2.2
Identity Lifecycle Management ....................................................................................35
6.2.3
Access Control ..............................................................................................................35
6.2.4
Monitor and Audit ........................................................................................................35
7
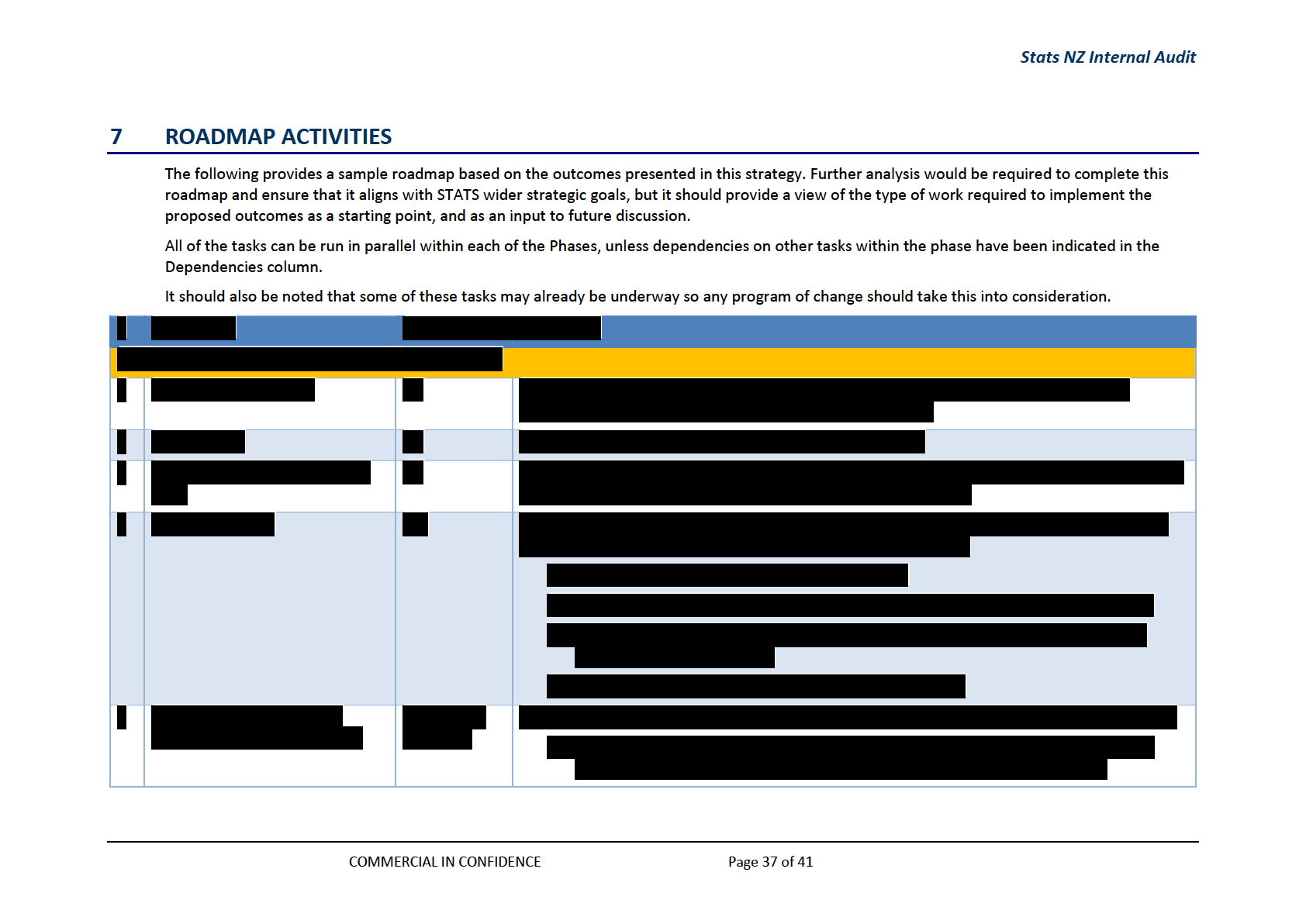
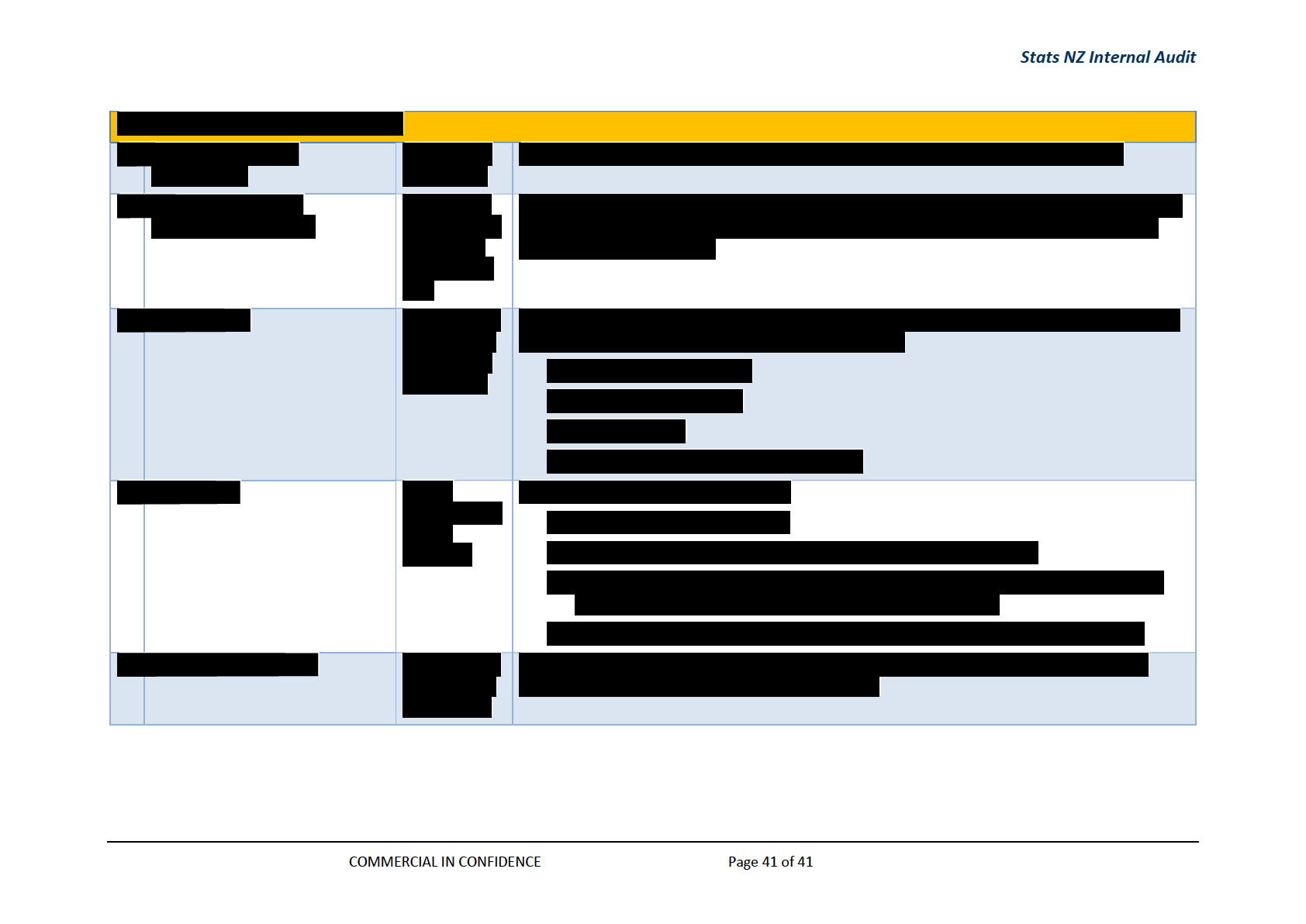
ROADMAP ACTIVITIES ................................................................................................... 37
Figure 1 - Identity and Access Management Towers of Capability ................................................ 8
Figure 2 - Current State Identity Management Components ......................................................13
Figure 3 - Current State Provisioning Flow A ...............................................................................15
Figure 4 - Current State Provisioning Flow B ...............................................................................16
Figure 5 - Current State Access Management Components ........................................................20
Figure 6 - Identity and Access Management Towers of Capability (Current) ..............................22
Figure 7 - Future State Reference Architecture ...........................................................................30
Figure 8 - Identity and Access Management Towers of Capability (Future) ................................34
COMMERCIAL IN CONFIDENCE
Page 4 of 41
Stats NZ Internal Audit
1
INTRODUCTION
Statistics New Zealand (STATS) has set a strategic goal to double the value of the data
provided for decision-makers. STATS plan to achieve this by adopting and promoting more
efficient and effective data practices, developing their data capability across the government
sector, and continuing to meet the needs of key customer groups, suppliers, and
stakeholders.
By 2030 STATS aims to create a tenfold increase in the value of data provided to New
Zealand.1
A key component for delivering to this goal, is the ability for STATS to enable access to data
for both internal and external identities in a secure and auditable manner.
The objective of this document is to provide an Identity and Access Management (IAM)
Strategy and Roadmap which STATS can use for the fol owing purposes:
1. Identify necessary identity processes to achieve the desired outcome.
2. Identify a single source of truth.
3. Guidance to move to a better identity state with a list of some potential quick wins
on the board.
4. Guidance around onboarding for Census staff.
UNIFY has worked together with the AXENIC and STATS teams to identify and understand the
high-level business requirements, assess the suitability of the existing product stack to
support the IAM desired outcome, and propose a roadmap to progress towards a better
identity state.
1 Statistics New Zealand – Information Systems Strategic Plan 2016 – 1st Edition
COMMERCIAL IN CONFIDENCE
Page 5 of 41
Stats NZ Internal Audit
2
EXECUTIVE SUMMARY
2.1 BACKGROUND
STATS has previously implemented several mechanisms to automate specific account
provisioning and de-provisioning actions and lifecycle management events. While these
point solutions function adequately, they do not provide an over-arching solution which is
necessary to ensure that end-to-end business processes and requirements are being met.
2.2 ENGAGEMENT OBJECTIVES
STATS has recognised that a whole-of-business perspective towards IAM may deliver
significant business benefits to a range of corporate stakeholders and business functions.
This engagement was commissioned to conduct a high-level analysis of the business and
systems environments within STATS and to identify opportunities for achieving business
benefits through the automation of Identity and Access Management.
Leveraging the expertise and experience of a specialist IAM consulting organisation, the task
was to present a strategy for IAM, a target IAM architecture and an implementation roadmap
that outlines the way in which the proposed IAM strategy should be implemented.
2.3 FINDINGS
In talking with the various stakeholders involved in this engagement, it became clear that a
fundamental shift has occurred within STATS regarding the importance of good identity and
access management practices. IAM is now seen as being a business enabler for moving the
organisation forward, as both a cloud/service consumer and as a service provider of
statistical data.
The recent severe Wellington earthquake (14 November 2016), and its aftermath have also
provided a catalyst for STATS to review its current state and identify any future needs in
order to better align its identity and access management practises with its business strategy.
Specifically, in terms of being a leader in the provision of data services to New Zealand.
2.4 RECOMMENDATIONS
COMMERCIAL IN CONFIDENCE
Page 6 of 41
Stats NZ Internal Audit
o
COMMERCIAL IN CONFIDENCE
Page 7 of 41
 Stats NZ Internal Audit
3
FUTURE STATE REQUIREMENTS
Stats NZ Internal Audit
3
FUTURE STATE REQUIREMENTS
Detailed business requirements for IAM are yet to be defined by STATS, however through
discussions with stakeholders a number of high-level requirements have surfaced. These,
along with some additional best practice requirements, form the basis for understanding the
capabilities that STATS will require from a future IAM solution.
3.1 HIGH-LEVEL FUTURE CAPABILITIES REQUIRED OF IAM
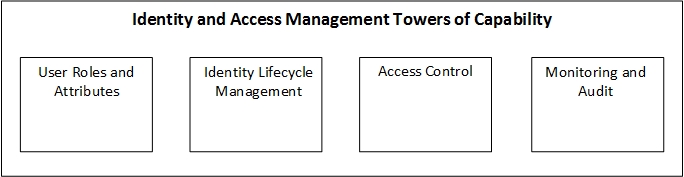
For the purpose of this strategy and roadmap, the capabilities required of IAM for STATS
have been split across four towers.
Figure 1 - Identity and Access Management Towers of Capability
3.1.1 User Roles and Attributes
This tower includes al the sources of information that can be used to create a complete
picture of an identity and its role and function within the organisation. This will include
Human Resources databases and other data sources that may hold relevant user attributes.
3.1.2 Identity Lifecycle Management
Managing the lifecycle of an identity through the organisation should be automated through
workflows and predefined processes based on associated attributes and roles assigned to the
identity. Identity Lifecycle Management should also provide a means for user self-service
where appropriate, including the provision of approval workflows for user requested
changes.
Identity Lifecycle Management should include:
• Automated User Provisioning.
• Automated user change based on attribute/role change.
• Automated de-provisioning.
User provisioning must have the ability to provision users in downstream access control
systems, other attribute stores, and applications with the appropriate attributes associated
with their role and function. The attributes associated to a user must also update in real-time
to reflect changes of a user's role or function.
3.1.3 Access Control
Access Control describes the control mechanisms for access to systems and applications
across the STATS ecosystem including internal systems, cloud-based systems and external y
facing systems.
Access Control should provide the fol owing:
• Ability to map to and enforce system and data classification policies.
COMMERCIAL IN CONFIDENCE
Page 8 of 41
Stats NZ Internal Audit
• Access Control based on associated security groups.
• Access Control based on other associated identity attributes – role, manager,
location, current function, etc.
• Just in time privileged access.
• Multi-factor authentication.
• Multi-factor step-up authorisation.
• Self-service password management.
3.1.4 Monitoring and Audit
The IAM platform components must provide means for monitoring and alerting on suspicious
access behaviours and should also provide for automated actions to be taken when such
behaviour is detected. Al access related activities are to be centrally logged.
The IAM platform components must provide a full audit trail of all identity changes and
provide a means of re-validation of user access.
COMMERCIAL IN CONFIDENCE
Page 9 of 41

Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 11 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 12 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 13 of 41

Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 15 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 16 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 17 of 41
Stats NZ Internal Audit
•
COMMERCIAL IN CONFIDENCE
Page 18 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 19 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 20 of 41

Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 22 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 23 of 41


Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 26 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 27 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 28 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 29 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 30 of 41
Stats NZ Internal Audit
6.1 FUTURE STATE REFERENCE ARCHITECTURE OVERVIEW
COMMERCIAL IN CONFIDENCE
Page 31 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 32 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 33 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 34 of 41
Stats NZ Internal Audit
COMMERCIAL IN CONFIDENCE
Page 35 of 41